No matter how tightly your computer is locked down, phishing continues to be an issue. Your anti-virus and/or email program will identify some of the culprits, but, because the phishers are always evolving, they can’t identify all of them. That’s why it’s important for you to be able to identify phishing attacks yourself!
What is “Phishing”?:
Phishing is defined very well by this Wikipedia article:
“Phishing is the attempt to acquire sensitive information such as usernames, passwords, and credit card details (and sometimes, indirectly, money) by masquerading as a trustworthy entity in an electronic communication. Communications purporting to be from popular social web sites, auction sites, banks, online payment processors or IT administrators are commonly used to lure unsuspecting public. Phishing emails may contain links to websites that are infected with malware. Phishing is typically carried out by email spoofing or instant messaging, and it often directs users to enter details at a fake website whose look and feel are almost identical to the legitimate one.”
Phone Calls:
- Your “bank” calls you to tell you about some unusual activity on your account and asks you to confirm your birthday.
- “Microsoft” calls you to tell you that your machine is out of date or has a virus and asks if they can access your machine to “fix” it.
Emails:
- Your bank sends you an email stating that someone has tried to access your online account. They’d like you to click on a link to prove that you’re you.
- The IRS sends you an email saying you have a refund coming.
- Yellow Pages needs to update your ad, when you’re not advertising with them.
- You get an email from yourself. (This is common. I get a lot of emails *from myself* asking if I want to purchase a product!
- Your insurance company asks you to click on a link for a new free service.
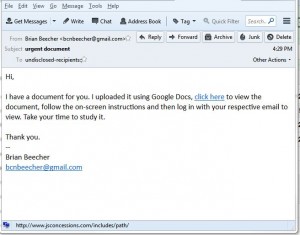
- Here’s an example of a phishing email I got the other day. It’s from a person I don’t know who wants me to open a Google document. The email program I use, Thunderbird, shows me where the link included in the document will take me. Notice that it is NOT a Google website! (Google docs always start with https://docs.google.com/…and.then.the.document.file.name ) Even if you don’t use Thunderbird, you can still hover your mouse over the link and most email programs will show you the full link.
Listen to your spider sense!
Even if everything looks okay, but you get a tingling sensation that it might not be, pay close attention. If you get *any* indication that the email is not from who it says it’s from, do some investigation. Is it supposedly from a friend? Call or text them and ask if they sent it? Is it from your bank? Call the number you have for your bank and ask!
Recent Phishing Scams:
IRS Warns of Phishing Tax Scams, Fake Emails
Anthem Warns Customers About “Phishing” Email Scam
Phishing Scam Spoofs BBB questionnaire; Businesses Warned Not to Click
Email Scam Alert from UC-Santa Cruz
What to Look For:
Every email & text that you receive should receive the once-over by you. Are you expecting that text / email / phone call? Are there misspellings? Are the links directed to where they say they are going? Is the grammar correct? Every unexpected phone call from an “authority” should be treated with suspicion, until you’ve determined their authenticity.
Be Safe out there Folks!
Make sure your anti-virus is always up to date and be careful of what information you provide to third parties. (If you do happen to inadvertently download a malware program, run your anti-virus right away.)
Chris Eddy of Geek For Hire, Inc. has been providing computer service to families and small businesses with Macs and PCs for the past fourteen years. He is highly rated by both the BBB (Better Business Bureau) and by Angies List. Geek For Hire, Inc. provides onsite service to the Denver/ Boulder/ Front Range area. They can provide remote service throughout North America.
